Building Access Control Optimized for Your Organization
How you welcome people – and how you keep them safe – has never been more important.
The right access control system is the cornerstone of your entryway security, enabling you to manage who enters, when, and how, with visibility to all that’s going on. Securitas Technology has the technology and expertise you need for your access control security: for global and small business, schools and campuses, manufacturing facilities, and for commercial enterprises of all kinds. Find your solution today.

Cloud-Based Access Control
Gain flexibility, scale and reliability
- Manage your system and user access privileges from anywhere
- Easily add new functionality whenever you need
- Peace of mind from built-in redundancy protect agains disasters
- Help control costs by eliminating or reducing on-site servers
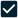
Biometric & Facial Recognition
Take access control credentials to a higher level
- Credentials that are unique to each user and which can’t be shared
- Greater security and accountability
- Supports consistent access policies

Mobile Credentials
Combine ease of use for your staff with strong security
- Fast, convenient access for users
- Issue or revoke credentials from anywhere, at any time
- Reduce dependence on physical credentials
Visitor Management
Extend your access control solution for greater protection
- Seamlessly integrate your visitor management with access control
- Automate screening processes & ensure compliance
- Protect your people and assets

Your Team is Ready for Mobile Phone Access Control. Are You?
of employees see traditional access control as a constraint
of employees use their smartphone in the workplace
of companies used mobile access control by the start of 2021
Access control is exactly what it says. It controls access to a specific area.
Drew Alexander
Getting Started with Access Control
Types of Access Control: How to Choose the Right One
When it comes to the different types of access control, it’s important to know that not all system types will be the best fit for your organization.
Learn More
What is Access Control?
Not sure where to start with access control technologies? Here’s the key information you need to find the right solution for your organization.
Learn More
Access Control Technologies Need-to-Know
Every entrance is unique and so is every organization, with multiple user needs and many choices for alerting, reporting, and monitoring. Here’s a guide to put your organization on the right path to effective security.
Learn More
How Access Control Security Supports Health & Safety
The right access security supports a healthy and safe environment for your employees and visitors. Securitas Technology can build you a commercial access control system that's tailored to your needs, leveraging these and other proven technologies:
- Mobile credentials: Reduce physical contact by storing access control cards on employees’ smartphones with cloud based access control.
- Touchless access: Incorporate facial recognition in place of keypads, swipe cards, or tags.
- Temperature and face mask detection: Integrate systems that detect temperatures and face masks to monitor the health of those who enter and exit your building.
Whether you operate a remote, in-person, or hybrid work model, access control system technology empowers you to keep your employees safe.
The Advantages of an Access Control System
Customize Access
Limit and personalize access to restricted areas to only those who need it, with the flexibility to grant secure temporary access to visitors.
Eliminate Key Management
Avoid the risk of lost or stolen keys getting into the wrong hands, and the hassle and expense of replacing keys or changing locks.
Gain Visibility
Know who’s entering and leaving, from which doors, and when. Activity reports can be accessed from wherever you are, whether remote or on-site.
Prioritize Your Business
Let us take care of your security – from design and installation through to integration and monitoring – so you can stay focused on your business.
Seamless Integrations
Integrate with other security systems, such as intrusion, video surveillance, HR databases, badging, visitor management systems, and more.
Maintain Health & Safety
Enhance your access control system with touch-free technology to provide a healthy environment for your employees and visitors
Experts in Access Control Solutions

Our highly skilled security technicians know how to deliver a state-of-the-art, integrated solution leveraging technologies from leading manufacturers such as Lenel, Honeywell, Software House, Brivo, Genetec, and others. Your system will be both highly effective and easily managed to help ensure the smooth flow of people throughout your building while maintaining the security of your business, employees, and property.

The right software solution is the backbone to any successful access control system – which is why it’s so important to have your software solution designed by experienced and certified engineers. Securitas Technology’s Software Solutions Group (SSG) is comprised of software engineers with decades of combined experienced in physical security who are ready to support your needs, from system planning to deployment.

Whether you’re experiencing theft or simply need to know who entered your facility, a detailed record of the comings and goings of employees, visitors, and vendors is essential to protecting your business. Securitas Technology helps ensure peace of mind by providing access control systems that give you an audit trail and thorough documentation of who was where, and when.

Our highly skilled security technicians know how to deliver a state-of-the-art, integrated solution leveraging technologies from leading manufacturers such as Lenel, Honeywell, Software House, Brivo, Genetec, and others. Your system will be both highly effective and easily managed to help ensure the smooth flow of people throughout your building while maintaining the security of your business, employees, and property.

The right software solution is the backbone to any successful access control system – which is why it’s so important to have your software solution designed by experienced and certified engineers. Securitas Technology’s Software Solutions Group (SSG) is comprised of software engineers with decades of combined experienced in physical security who are ready to support your needs, from system planning to deployment.

Whether you’re experiencing theft or simply need to know who entered your facility, a detailed record of the comings and goings of employees, visitors, and vendors is essential to protecting your business. Securitas Technology helps ensure peace of mind by providing access control systems that give you an audit trail and thorough documentation of who was where, and when.
Access Control FAQs
Access control refers to the practice of permitting or restricting individuals’ physical access to a building, site or even to specific areas and rooms. These systems can be applied to any physically contained points, such as doors, gates, barriers, fences, turnstiles and even elevators. They can be simple standalone systems controlling one or two doors, or they can be an integrated network that covers multiple buildings.
As the name implies, an access control system controls who enters a site/building and specific areas within those premises and at what time, barring unauthorized visitors without impeding the flow of those who are authorized.
Securitas Technology is proud to provide multiple options when it comes to finding the best access control solution for your business, ranging from door intercoms and card and proximity tokens to biometric and facial recognition from leading manufacturers.
Access control systems enable multiple layers of security and provide more detailed information to owners and managers of facilities. They replace mechanical keys as the main way to control access to and within a building. Access can be tailored to each individual, and modified or revoked at any time. The access control system will also provide an audit trail of "who, when, where" for anyone in the access control system. Mechanical keys do not provide an audit trail or security of the key itself. Keys may be copied easily, whereas access control systems are designed for easy modifications, especially lost or missing cards.
Your business needs access control if you have employees, suppliers or other visitors and you want to control the entrant’s access a certain location, room, area or site, or limit that access to certain times or days.
Preventing unauthorized access to a site helps protect your people, property and assets from damage or theft. Additionally, it may also act as a safety measure, preventing people from going near a potentially dangerous area or equipment.
Access control systems can consist of:
- Swipe-card door lock system, fob or RFID readers
- Touch screens or keypads
- Remote access or smart locks
- Mobile credentials
You can combine technologies within the management systems for increased reliability and convenience.
When it comes to managing your access control system, Securitas Technology provides multiple options. Depending on what’s best for your business, we can provide either a software- or web-based management application, which your team can use to easily manage your access control security. Or, you can delegate administration of your access control system to our team of experienced professionals.
Basic or Standalone System
- A simple way to control one or two doors
- Consists of a physical server and connected computer on the business premises
- Right for: Smaller business or specific locations with no need to connect to other sites
Networked System
- Two or more systems networked over a building, several sites or worldwide
- Managed from a central location with a data server and networked computers
- Right for: Businesses with many offices or sites
Local Cloud-Based System
- Data is held in an on-site server and accessed via a portal website
- System is accessed through the cloud from anywhere, and the hardware is on-site
- Right for: Smaller companies requiring flexibility
Cloud-Hosted System
- Access control server is managed at an off-site data center
- Physical access control, such as key card readers, are still in place on-site
- Right for: Businesses that prefer to outsource the management and maintenance of a networked access control system, or need the flexibility to manage many remote sites
Fully Managed Cloud System
- A monitoring center provides real-time building access and fully manages your access control
- Entirely cloud-based and enables a remote security company to manage the complete system for you
- Right for: A business that needs an entirely cloud-based system
Our skilled engineers can integrate your chosen access control solution into one system for all your security needs, including:
- Access Control
- CCTV
- Intruder Detection
- Fire Detection
- Time and Attendance
- and more
Access control systems provide audit trail reporting of activity by each individual that is using their credential in the access control system. Most access control platforms will provide information in the form of "Who, Where, When" at a minimum. More advanced access control platforms provide an even greater range of information.
Most commercial access control systems are not designed for self-installation. Access control systems are complex with multiple technologies and hardware needing to work together as a single system. A working knowledge of electronics, electrical wiring, networking, and computer hardware is required for commercial grade access control platforms.
A typical access control system for business or commercial applications requires the installation of electronic hardware components and cabling infrastructure. The hardware components will consist of circuit boards, card readers or other identification readers, locking hardware and miscellaneous supporting components. Depending upon the scale of the project, installation may take a few days or extend to a period of months. Most access control systems will require network or internet access for management and reporting purposes.
A proximity system is a fob, card or other device which uses encrypted RFID technology. When the device is presented to the reader, the reader passes the device’s code to the access controller. The controller compares the data being presented with that held in the system’s database and then permits or denies access accordingly. The data can be very specific, only permitting access to that door to that person at a set date/time.
The existing mechanical keying system will remain in place in most access control systems, and any existing functioning keys can still unlock the door(s). It is best practice to change or modify the keying system when deploying an electronic access control system. Keys should be reserved for use by specific individuals and for emergencies only.
Get More from Access Control with These Solutions

Video Surveillance
Keep an eye on your business from anywhere, any time with Securitas Technology, one of the top verified video surveillance companies.

Visitor Management
Create and automate a professional, safe, and inviting visitor experience.

Security Monitoring Services
Securitas Technology’s 24/7 security monitoring services help ensure rapid response to alarms, extending your security team, protecting your people, and empowering your business to operate securely and efficiently.

Intrusion Detection System
Deter potential intruders from your premises with a reliable intrusion system.

Electronic Article Surveillance (EAS)
Electronic article surveillance solutions for reducing theft, tracking inventory & improving the customer experience.
Shrinkage Control & Retail Loss Prevention
Prevent business loss due to internal theft and retail shrinkage with retail loss prevention systems. Loss prevention in retail requires a comprehensive approach, combining technology, employee training, and strategic monitoring to ensure a secure environment for both staff and customers.
Get Started with Access Control
Our Access Control Insights
The 3 Cs of Access Control
Access control means selectively restricting access to a specific space, and these are the guidelines you should use.
Learn More
The 4 Most Common Types of Access Control Credentials
Modern electronic access control systems, whether on-premise or cloud-hosted, offer a variety of ways to authenticate users and grant them access to a space. Keep reading to learn about four of the...
Learn More
Why Access Control Systems are More Important than Ever
Health and safety protocols, social distancing, and the advent of remote work have prompted innovation in the security industry.
Learn More